Industry Targeting and Trends
Primary Targets and Emerging Threats
Banking institutions continue to bear the brunt of advanced attacks, representing nearly a third of all sophisticated intrusions. Yet the medical sector experienced the most dramatic surge in targeting – jumping almost 50% since last year – as health records command premium prices in underground markets.
Global Operations and Detection Times
These criminal enterprises now strategically distribute operations globally, establishing presence across numerous jurisdictions to frustrate investigative efforts and legal consequences. Security researchers documented 18 previously unidentified major threat collectives that surfaced within the past twelve months.
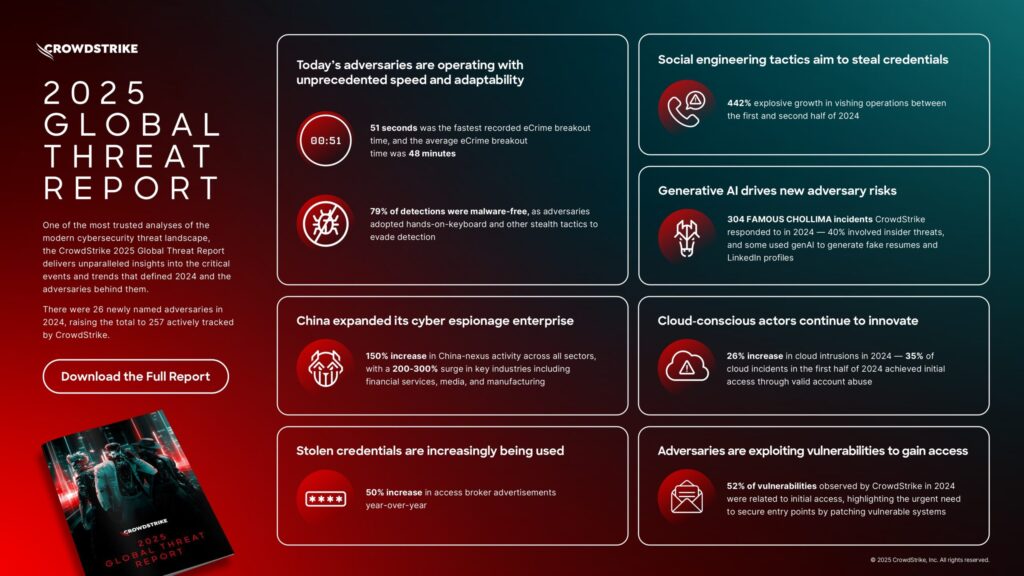
The timeframe attackers lurk undetected within compromised networks has contracted to approximately one week. This trend reflects both enhanced security monitoring and attackers’ strategic shift toward rapid-strike operations with quick financial returns.
Evolution of Attack Methodologies
Technical Sophistication
Technical methods continue advancing in complexity. Modern threat actors increasingly utilize authorized administrative tools and mainstream cloud platforms, effectively camouflaging malicious activity within legitimate business traffic.
Supply Chain Vulnerabilities
Attacks targeting vendor networks remain devastatingly effective, as adversaries pivot away from hardened primary targets toward their more vulnerable business partners and service ecosystems. Research shows these indirect compromises have grown by more than a third year-over-year.
AI in the Attack Landscape
AI has predictably become both shield and sword. Defenders use it to spot anomalies, while attackers employ it to craft hyper-personalized phishing campaigns and to probe defenses automatically at scale.
Defensive Strategies for Organizations
The report offers clear guidance for organizations facing this new breed of adversary. Static defenses no longer suffice against opponents who operate with business-like adaptability. Security programs must embrace continuous evolution, threat intelligence integration, and proactive threat hunting.
Employee training remains crucial but must evolve beyond basic awareness to cultivating a security-first culture where unusual activities are promptly reported and investigated.
The Future of Cybersecurity Defense
What makes the 2025 landscape truly different is how these criminal enterprises have embraced operational excellence. They conduct market research, optimize their attack chains, and even perform customer satisfaction surveys after successful ransomware payments to improve their “services.”
The path forward requires security teams to match this level of organizational sophistication. As these adversaries continue professionalizing their operations, our defenses must evolve accordingly—not just technically, but structurally and culturally as well.
Source:
CrowdStrike
Conclusion
The enterprising adversary represents the new normal in cybersecurity—opponents who bring boardroom-level strategic thinking to digital crime. Meeting this challenge requires nothing less than the same level of business acumen applied to our defensive posture.